Overview
About Forensic Explorer™
Forensic analysis software
Suitable for new or experienced investigators, Forensic Explorer combines a flexible and easy to use GUI with advanced sort, filter, keyword search, data recovery and script technology. Quickly process large volumes of data, automate complex investigation tasks, produce detailed reports and increase productivity. Manage all aspects of the investigation, including:

• File System Analysis
• Keyword & Index Search
• AI Graphics Analysis (CSAM detection)
• Live Boot Virtualization
• Registry
• Report
Key Features
- Forensic Explorer includes a stand-alone licenses of: FEX-Triage, FEX-CLI and Mount Image Pro (MIP)
- No major version upgrade costs (valid maintenance give access to the latest build).
Software features include:
Anti-Virus: |
In built Cisco Clam anti-virus. |
Artificial Intelligence |
Forensic Explorer uses advanced AI-powered image recognition and delivers high detection accuracy with near-zero false positives. Includes a CSAM detection addon for law enforcement. |
Bookmark: |
Bookmark, flag, or categorize potential evidence. |
Case Management: |
Create, save and load case files. |
Data Access: |
Access all areas of physical or imaged media at a file, text, or hex level. View and analyze system files, file and disk slack, swap files, print files, boot records, partitions, file allocation tables, unallocated clusters, etc. |
Data Carving: |
Inbuilt data carving tool to carve more than 300 known file types. |
Data Views: |
Powerful data views including:
|
Email: |
Email support for PST, OST, EDB, MBOX formats. Full keyword and index search capabilities for email. |
Export: |
Export files to disk, or direct to .L01 forensic evidence files. |
GUI: |
Detach drag and drop views for a customized work-space on multiple monitors. Save and load personal work-space configurations to suit investigative needs. |
Hash: |
Apply hash sets to a case to identify or exclude known files. Hash individual files for analysis.
|
Index: |
Built-in DTSearch index capability. |
Keyword Search: |
Cluster, sector, or byte level keyword search of entire media using text, regex or hex expressions. |
Language: |
Forensic Explorer is Unicode compliant. Investigators can search and view data in native language format such as Dutch or Arabic. |
Language GUI: |
FEX GUI language can be set to EN, DE, ES, FR, ID, TR, ZH on install (language option set in registry). |
Metadata: |
Extract and report file metadata, including EXIF, GPS, MS Office and more. |
Mount (MIP): |
Mount forensic image files as a Windows drive letter (Mount Image Pro). Full access to deleted, system, unallocated, etc. Full CLI capabilities. |
RAID: |
Work with physical or forensically imaged RAID media, including software and hardware RAID, JBOD, RAID 0, RAID 5, RAID 6. |
Recovery: |
Recover deleted folders and partitions. |
Registry: |
Open and examine Windows registry hives. Filter, categorize and keyword search registry keys. Automate registry analysis. |
Reporting: |
Custom report builder with pre-defined reporting templates. |
Scripting: |
Inbuilt powerful Delphi scripting language. Inbuilt scripts for:
|
Servlet (Network): |
Connect to and examine remote drives using a deploy-able network servlet. |
Shadow Copy: |
Easily add and analyze shadow copy files. Learn more about Forensic Explorer Shadow Copy Volumes. |
Signature: |
Forensic Explorer can automatically verify the signature of every file in a case and identify those mismatching file extensions. |
Triage: |
Automatically triage and report on common forensic search criteria. |
Virtual Live Boot: |
Virtualize Windows and MAC forensic image and physical disks using VirtualBox or VMWare. |
Yara Rules |
Yara rules enable investigators to quickly and efficiently identify malware and other forms of malicious software within digital evidence. By leveraging Yara Rules, examiners can apply a set of customizable, text-based rules that are designed to match specific data characteristics. |
System Requirements
A Forensic Explorer purchase includes Mount Image Pro (Mount Image Pro is installed as a separate stand alone product). It is recommended that Forensic Explorer and Mount Image Pro be run with the following minimum system requirements:
- Intel® Core i7 or i9
- 16 GB RAM
- 64 bit Windows 10
- Install and run as local administrator user.
Virtual Live Boot requires VirtualBox or VMWare as part of the virtualization process.
Activation
- Forensic Explorer and Mount Image Pro are activated with a Wibu Codemeter (www.wibu.com) USB dongle (dongle can contain one or more licenses). The dongle can be local or remote (accessible via an I.P. address).
- Supports network licensing, e.g. a single dongle contains multiple licenses to activate lab computers on demand.
Supported File Formats
Forensics Explorer supports the analysis of the following image formats:
- AFF v4
- Apple DMG
- DD (RAW, BIN, IMG)
- EnCase® (E01, L01, Ex01)
- FTK® (E01, AD1 formats)
- ISO (CD and DVD image files)
- Macquisition
- NUIX File Safe (MFS01)
- Oxygen Backups (OCB)
- ProDiscover®
- SMART®
- Virtual Disk Image (VDI)
- Virtual Hard Disk (VHD, VHDX)
- VMWare® (VMDK)
- XWays (E01, CTR)
- ZIP
Supported File Systems
Forensic Explorer supports analysis of:
- Windows FAT12/16/32, exFAT, NTFS,
- Macintosh HFS, HFS+, APFS
- EXT 2/3/4
- Hardware and Software RAID: JBOD, RAID 0, RAID 5, RAID 6
Encryption Support
Unlocks the following (password or recovery key required):
- Bitlocker
- FileVault 2
Processing
- Fully Threaded Application
- Multi Core Processing
Screenshots
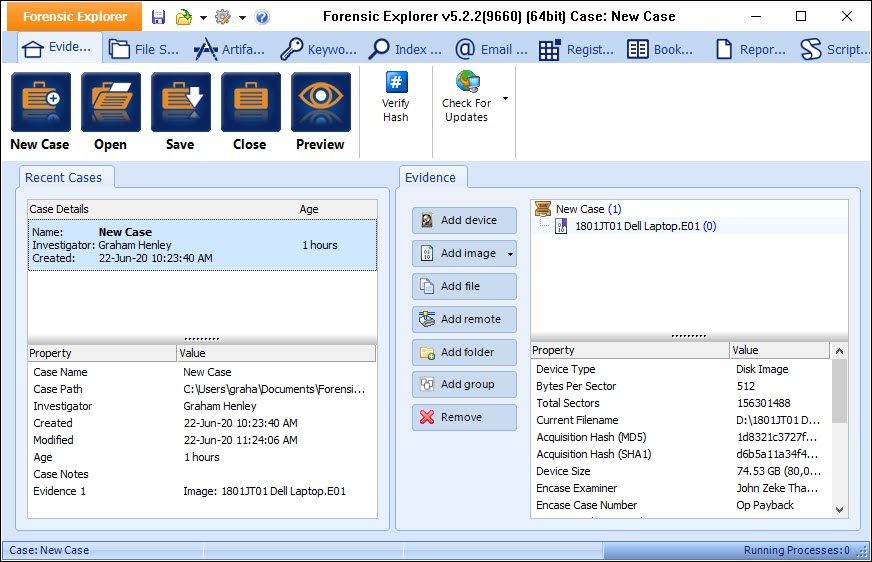
Evidence Module
Add and manager evidence sources including devices, forensics images, files and remote data:
File System Module
The File System module is where much of the analysis takes place. Use filtering, sorting, and data views (Video view shown) to quickly locate evidence:

Reports Module
Quickly produce complex reports that can be saved as templates and used for future investigations:

Purchase & Licensing FAQs
License Type
A Forensic Explorer license is a perpetual license*. The license does not expire.
A purchase includes a 12 months Software Maintenance and Support (SMS). SMS provides regular software updates and access to technical support. Additional SMS can be purchased and is added from the existing maintenance date.
Educational pricing is available to students or educators who participate in a recognized tertiary computer forensics course. Follow the Academic Program link in the footer of this page.
Wibu CodeMeter Activation Dongle (Wibu Dongle)
The software is activated by a license on a Wibu Dongle. A Wibu Dongle can hold one or more licenses. It can be:
- Connected locally (i.e. plugged into the computer in use); or
- Connected to a remote computer and accessed over a network.
License Management
Wibu Dongle licenses are managed using the GetData License Manager software (download here). The License Manger is used to:
- View license information.
- Add a license to a Wibu Dongle.
- Rename a dongle.
- Apply firmware updates.
A lite version of Wibu CodeMeter software is installed with GetData products. A full version of CodeMeter User Runtime for Windows is available from the Wibu website. It can be used to:
- Configure a computer and dongle to be used as a license server;
- Configure a computer to be used as a network client;
- Rename a dongle, apply firmware updates, and other maintenance functions.
Learn more about license management here.
License Delivery
Wibu Dongles are shipped worldwide by FEDEX. Web tracking information is provided for each shipment. Courier delivery costs are included in the checkout process.
